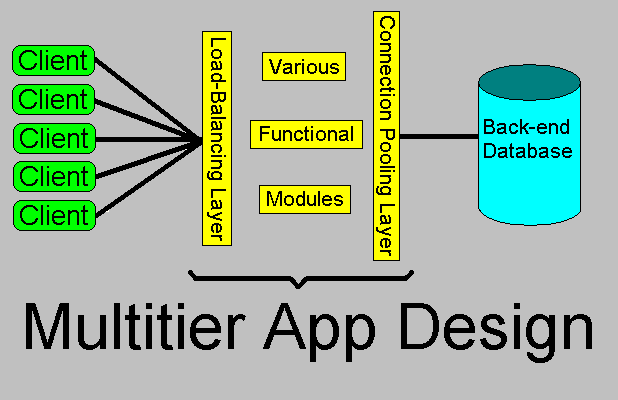
Multitier Architectal Issues
Where do we place AAA measures, and what assumptions does
their placement imply?
Exploitation by telnet and strings;
what threats are we countering (thin vs. thick client)?
This page is maintained by Foofus.
Send comments or questions to foofus@foofus.net.